Password Managers (KeePass)
Why You Should Use a Password Manager
- You don’t need to remember hundreds of passwords
- You only need to remember one master password
- You can have different passwords for different websites and don’t need to worry about forgeting them
Popular Password Managers[1]
| In-browser based | Commercial based |
|---|---|
Google Chrome  |
Dashlane  |
Mozilla Firefox  |
Keeper  |
Safari  |
1Password  |
Microsoft Edge  |
KeePass  |
Password Managers Workflow

Difference between automatic autofill and manual autofill
Automatic Autofill:
- Does not wait for user interaction
- One click: submit button
- Vulnerable to vatious sweep attacks
Manual Autofill:
- Wait for user interaction
- Two clicks: select correct account + submit credential
- More secure
Threats, Attacks and Defences
Redirect Sweep Attacks
- Resirect sweep attack is only gainst automatic autofill password managers. When a taget user connect to a wifi hotspot that is controlled by an attacker, the attacker will trick the password manager to fillin the password and send the password back to the attacker.[2]
- Defence:
- Require user interaction before autofilling
- Login page over HTTPS
Cross Site Scripting(XSS) Injection
- An attacker inject JavaScript code to login page then the program gets credentials and send back to the attacker.[3]
- Defence:
- Explicit user interaction to trigger fill-in action
- URL matching and form matching
Other Attacks
- iFrame sweep attack
- Window sweep attack
- Attack amplification via password sync
Keepass Password Safe
download KeePass KeePass Password Safe is a free, open sourcem light-weight password manager.[4]
Why use Keepass
- Third party tool
- Manual autofill (secure)
- Free and open-source
- Strong compatibility (it primarily used in Windows devices, but it supports all Operating Systems like Mac, IOS, Android, Linux)[5]
- Lightweight (it wouldn’t occupy many memory of your device)
- Easy to use (it has clear User Interface, so it would be easy-to-manage even for the beginner)
How does Keepass work
- The KeePass stores all the passwords in a database file, which is locked with a master key. [4]
- The database file is encrypted using the best and most secure encryption algorithms, which are AES and Twofish.
- KeePass uses SHA-256 to hash the master key components.
Encryption algorithms
AES
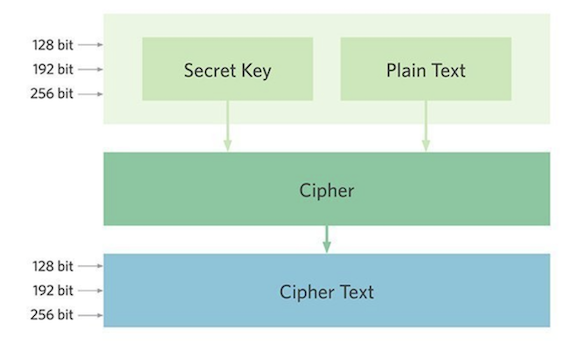
- It uses symmetric block cipher (same key for both encryption and decryption)
- It proved to be useful to protect sensitive data
- National Security Agency (NSA) utilize AES encryption to protect their sensitive information [6]
- Many governments and institutions are using AES to protect their data [7]
- It hard to brute force, since it accepts key sizes more than 128 bits
Twofish
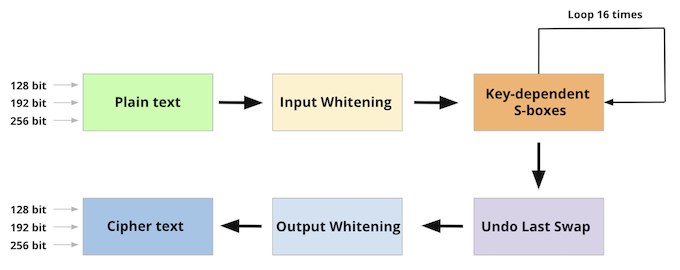
- It uses symmetric block cipher (same key for both encryption and decryption)
- It Trade-offs between key-setup time and encryption speed that make it unique among the AES candidates [8]
- There have been a few attacks on Twofish. However, It did not constitute a true cryptanalysis [9], according to its creator, Bruce Schneier.
- It hard to brute force. Similar to AES, since the TwoFish supports key sizes of more than 256 bits, it is resistant to brute force attack[10]
SHA-256
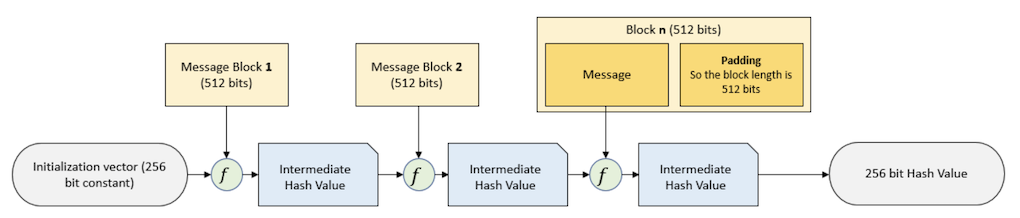
- SHA-256 is a patented cryptographic hash function
- It is a keyless hash function that takes information and generates random characters with length 256 bits [11]
- It is almost impossible to reconstruct the initial data from the hash value.
- A brute-force attack would need to make 2256 attempts to generate the initial data. [12]
- It is unlikely to have two same hash value of two inputs.
- With 2256 possible hash values, the likelihood of two being the same is infinitesimally, unimaginably small. [12]
- The avalanche effect.
- A minor change to the original data will make its hash value change a lot. So two similar inputs will not likely generates similar hashed output through AHS-256.
KeePass Demo
- A minor change to the original data will make its hash value change a lot. So two similar inputs will not likely generates similar hashed output through AHS-256.
- How to use KeePass
References
[1] D. Balaban, “Comparing In-Browser-Based, Commercial Password Managers,” eWEEK, 18-Feb-2021. [Online]. Available: https://www.eweek.com/search-engines/comparing-in-browser-based-commercial-password-managers/. [Accessed: 03-Mar-2021].
[2]D. Silver, S. Jana, and D. Boneh, “Password Manager: Attacks and Defenses,” 23rd USENIX Security Symposium, Aug 20 - 22, 2014.
[3] “Preventing XSS Attacks through CSS Whitelisting,” Powered by MediaWiki. [Online]. Available: https://www.mediawiki.org/wiki/Preventing_XSS_Attacks_through_CSS_Whitelisting. [Accessed: 03-Mar-2021].
[4]D. Reichl, KeePass Password Safe. [Online]. Available: https://keepass.info/. [Accessed: 03-Mar-2021].
[5]“Managing my passwords with KeePass and OwnCloud,” Managing my passwords with KeePass and OwnCloud | Gabriel’s Tech blog. [Online]. Available: https://www.detassigny.net/posts/3/managing-my-passwords-with-keepass-and-owncloud. [Accessed: 03-Mar-2021].
[6] M. from R. Thomas, R. Thomas, Eyal Gruner | 3 days ago, Kyle Marchini | 4 days ago, Y. E. | F. 23, Richi Jennings | 1 day ago, R. J. | F. 22, and R. J. | F. 19, “Advanced Encryption Standard (AES): What It Is and How It Works,” Security Boulevard, 24-Apr-2020. [Online]. Available: https://securityboulevard.com/2020/04/advanced-encryption-standard-aes-what-it-is-and-how-it-works/. [Accessed: 03-Mar-2021].
[7] M. Cobb, “What is AES Encryption and How Does it Work?,” SearchSecurity ,17-Apr-2020. [Online]. Available:https://searchsecurity.techtarget.com/definition/Advanced-Encryption-Standard#:~:text=TheAdvanced Encryption Standard (AES,cybersecurity and electronic data protection.[Accessed: 03-Mar-2021].
[8]B. Schneier, Schneier on Security. [Online]. Available: https://www.schneier.com/academic/archives/1998/12/the_twofish_encrypti.html. [Accessed: 03-Mar-2021].
[9]S. Encrypt, “Twofish Encryption: What Is It?,” Choose To Encrypt, 07-Mar-2019. [Online]. Available: https://choosetoencrypt.com/tech/twofish-encryption/. [Accessed: 03-Mar-2021].
[10]D. Miladinović and R. R. Rosario, “Twofish vs AES Encryption,” Cloudstorageinfo.org, 22-Dec-2020. [Online]. Available: https://cloudstorageinfo.org/twofish-vs-aes-encryption. [Accessed: 03-Mar-2021].
[11]“SHA-256 Algorithm Overview,” Solarwinds MSP, 26-Jan-2021. [Online]. Available: https://www.solarwindsmsp.com/blog/sha-256-encryption#:~:text=SHA-256 is a patented,that is 256 bits long.&text=In cryptographic hashing, the hashed,its original 512-bit form. [Accessed: 03-Mar-2021].
[12]f4tca7, “Introduction to the SHA-256 hash function,” Steemit. [Online]. Available: https://steemit.com/cryptocurrency/@f4tca7/introduction-to-the-sha-256-hash-function. [Accessed: 03-Mar-2021].