Password Recovery with Hashcat
Presented by Fortunate Eze, Xinying Zhou & Kshitija Patel
Hashcat
Hashcat is a password recovery tool. It had a proprietary code base until 2015, but was then released as open source software. Versions are available for Linux, OS X, and Windows. Examples of hashcat-supported hashing algorithms are LM hashes, MD4, MD5, SHA-family and Unix Crypt formats as well as algorithms used in MySQL and Cisco PIX.
Previously, two variants of hashcat existed:
-
hashcat - CPU-based password recovery tool
-
oclHashcat/cudaHashcat - GPU-accelerated tool (OpenCL or CUDA)[1]
With the release of hashcat v3.00, the GPU and CPU tools were merged into a single tool called hashcat. The CPU-only version became hashcat-legacy[2]. Both CPU and GPU now require OpenCL.
Hashcat is capable of cracking over 200 hashing algorithms. Many of the algorithms supported by hashcat-legacy (such as MD5, SHA1, and others) can be cracked in a shorter time with the GPU-based hashcat[3]. However, not all algorithms can be accelerated by GPUs.
Hashing Algorithms
A hashing algorithm is a cryptographic hash function. It is a mathematical algorithm that maps data of arbitrary size to a hash of a fixed size.
A hash function algorithm is designed to be a one-way function, infeasible to invert[4].
Note that:
-
Hashes are not produced at random. They follow a specific mathematical calculation and are constant for the same plain text password and hash function. What this means is that a plain text password ‘secret’ hashed using MD5 (for example) will always produce the same hash (output) regardless of the number of times the hashing process is done.
-
Hashes, unlike cyphers cannot be reverse engineered. It is not possible to directly manipulate a hash to obtain the plain text password.
-
While hashes are constant for the same plain text, They vary significantly for passwords with very little differences. For example, a password ‘John’ (Uppercase ‘J’) will produce a significantly different but constant hash from a password ‘john’ (lowercase ‘j’) using the same hashing function/algorithm for both passwords. This is called an avalanche effect.

Hashing passwords provide an extra level of security over the plain text form of storing passwords. If a server is attacked, the attacker cannot immediately see the plain text passwords of the users of the service, rather, they will only get encrypted (hashed) forms of the passwords.
How Hashcat cracks password hashes Since hashes cannot be reverse engineered or ‘decoded’, hashcat uses a ‘guess’ method to crack passwords. Hashcat takes in a hash to be cracked, the algorithm used to make the hash, and depending on the mode of attack, takes a guess password, hashes it using the same algorithm that made the original hash (hash to be cracked) and checks if the newly obtained hash matches the original hash. If they are a match, it means that the guess password is the password that produced the original hash. If they don’t match, hashcat retries this process using a new guess password.
In Hashcat, there are two main ways to crack a hash:
- Brute-Force Attack
- Straight Attack
- Combinator Attack
a) Brute-Force Attack attempts to guess the password with all possible combinations[3]. If you have a 6-digit numeric password, a brute-force attack will try all the possible combinations from 000000 to 999999. Your password must be included in this range (000000-999999). A brute-force attack if done right will eventually crack the password but the time it will take to achieve this greatly depends on the password and the hardware used to perform the attack.
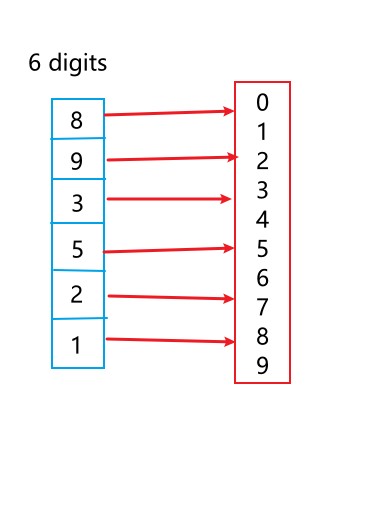
Some form of social engineering can be performed prior to making the attack in order to get an idea of what the target password could be. This could provide a guide for the attacker and make the brute-fore attack process a lot faster. Long, random character passwords could take forever to crack using a brute-force attack on a basic commodity hardware, but this time can be exponentially decreased using super computers.
For brute-force attacks, hashcat uses a mask. A mask is specific set of rules used to tell your cracking utility which parts of a key space should be used. With masks, you can tell hashcat what range and type of characters to permutate and use as it’s ‘guess’ to crack the password. You can learn about masks and how to use them here.
b) Straight Attack, also known as a dictionary or wordlist attack. The main idea of a dictionary attack is to use a wordlist file which usually includes many commonly used passwords. A compiled list of passwords obtained from previously attacked servers like the rockyou.txt wordlist can be make the process even more effective.
In a basic wordlist attack, hashcat takes each word in the provided wordlist as it’s password guess, hashes it using the same hashing algorithm used to make the hash to be cracked and compares the new hash against the original hash. If there’s a match, the guess password is the correct password, else, hashcat takes the next word in the wordlist and tries again.
In a straight attack, rules can be specified to add extra permutations to the words in the wordlist. With rules, we can tell hashcat to not just check for the words in the wordlist but to add some variety as well and check with those varieties. For example, if we have a word ‘secret’ in the wordlist, we can specify a rule that tries:
- ‘secret’ - the one on one match with the wordlist
- ‘Secret’ - with the first letter in uppercase
- ‘(0 - 9)secret’ - numbers 0 - 9 prepended before secret (i.e. 1secret, 2secret, 3secret, etc)
- ‘secret(0 - 9)’ - numbers 0 - 9 appended after secret (i.e. secret1, secret2, secret3, etc.)
- ‘s3cr3t’ - with letter ‘e’ replaced with ‘3’
You can learn more on how to define rules here.
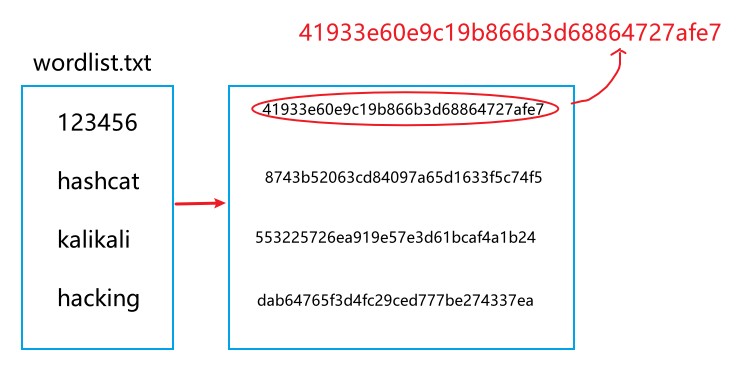
In the image below, the hash to be cracked is the text in red and the text ‘123456’ in our wordlist - when hashed - matches the original hash, therefore ‘123456’ is the correct password.
c) Combinator Attack involves the combination of two wordlists to obtain a password guess. Hashcat takes a word ‘secret’ from wordlist1 and takes another word ‘place’ from wordlist2 and combines them to form ‘secretplace’, then uses this as the guess, hashes it and compares against the original hash. A combinator attack generally takes longer than a basic single wordlist attack for obvious reasons.
Usage of Hashcat
The basic usage of hashcat requires at least four arguements:
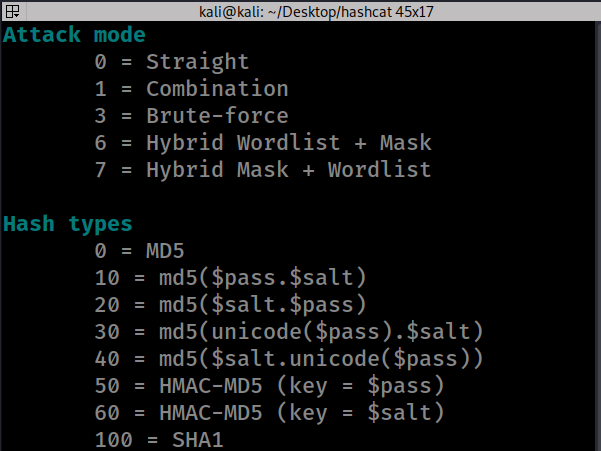
- –hashtype (-m) This specifies the hashing algorithm that hashcat should use against the hash to be cracked. For this to work, the choice hashing algorithm should be the same with the one that was used to make the original hash. Hashcat is able to crack over 200 different hash functions.

- –attack mode (-a) This specifies the method hashcat should use to perform the attack, e.g. Straight Attack (Wordlist Attack), Brute-force Attack, Combination Attack, etc.

-
The file containing the hash to be cracked or the hash itself (eg, hashes.txt or 200ceb26807d6bf99fd6f4f0d1ca54d4)
-
The wordlist or mask to be used for the attack (e.g rockyou.txt or ?a?a?a?a) Some optional arguments include -r (used to specify rules), -o (used to specify a file to save cracked passwords, -i (used in bruteforce attacks to specify increments in password ranges). —
Demonstration
For our demonstration, we will use MD5 (-m 0) as our hash function. This is because MD5 is a fast hash function and we will be able to make our password cracking much quicker with commodity hardware.. A fast hash function has the advantage of authenticating users quickly but also has the disadvantage of being cracked quickly.
1. Basic wordlist attack
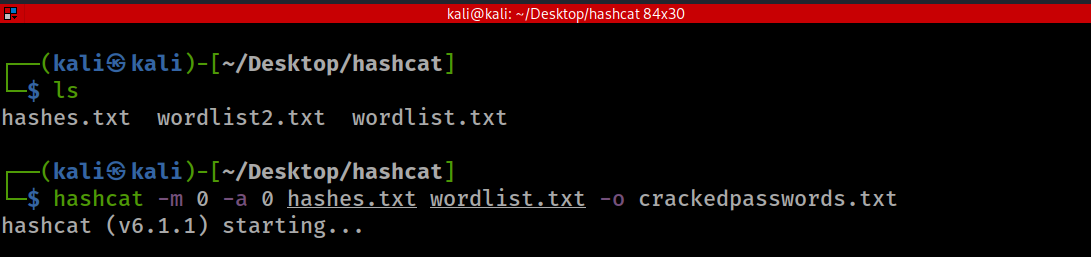
- -m 0 = MD5
- -a 0 = Straight attack mode
- hashes.txt contains all our MD5 hashses
- wordlist.txt contains the top 3000 words in English Language obtained from here. We are using a fairly small wordlist for quicker results. Note that in the real world, wordlists get over tens of millions of words.
- -o crackedpassword.txt = Specifies an output file to store our cracked password
 Here we run a basic wordlist attack and we crack the passwords that are one on one matches with words in the wordlist.
Here we run a basic wordlist attack and we crack the passwords that are one on one matches with words in the wordlist.
2. Wordlist attack with rules

- -r /usr/share/hashcat/rules/best64.rule = best64.rule is a default rule that comes with hashcat. It is located in the path shown above but could be different on your machine. Use find to search for the location of yours.
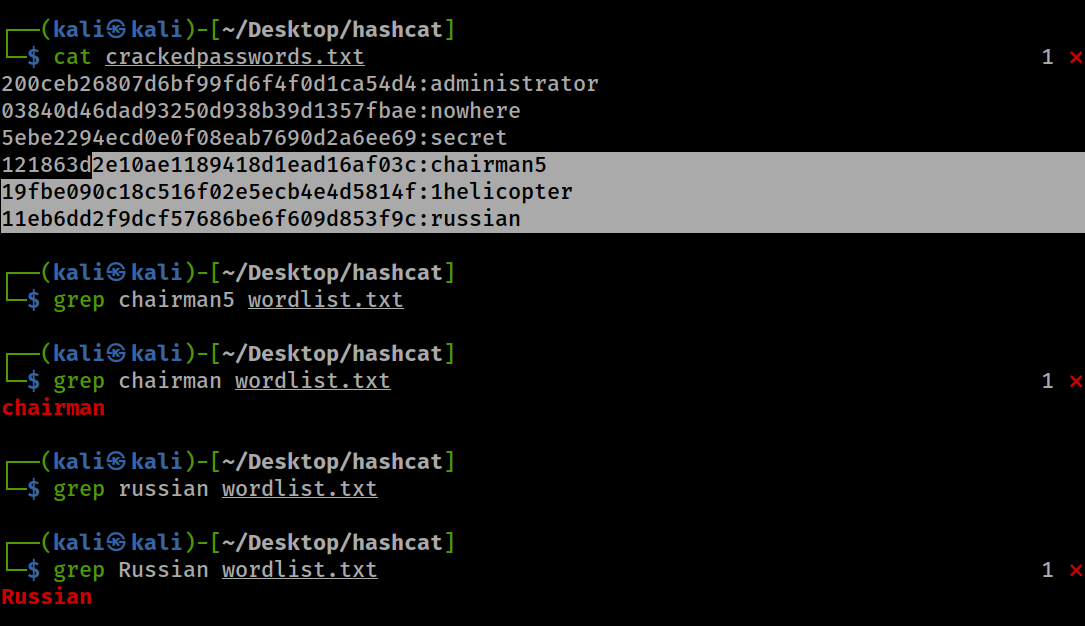
- You can see that ‘chairman’ is in the wordlist, but ‘chairman5’ isn’t. However, we were able to crack ‘chairman5’ using the wordlist and a set of rules. The rule here tried the one on one match ‘chairman’ and appended numbers to it and retried.
- Same applies to ‘russian’. The lowercase version is not in the wordlist but our rules cracked it by trying it with the first letter in uppercase.
3. Combinator Attack
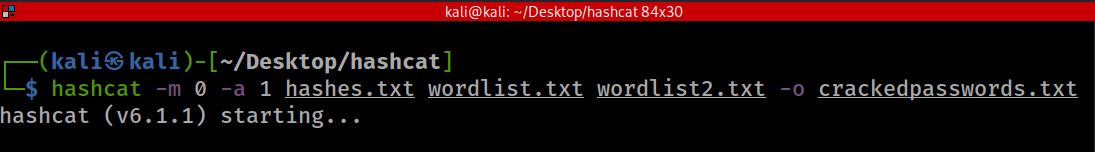
- Wordlist2.txt is just a clone of wordlist.txt. We made a copy for simplicity. A combinator attack requires two wordlists.
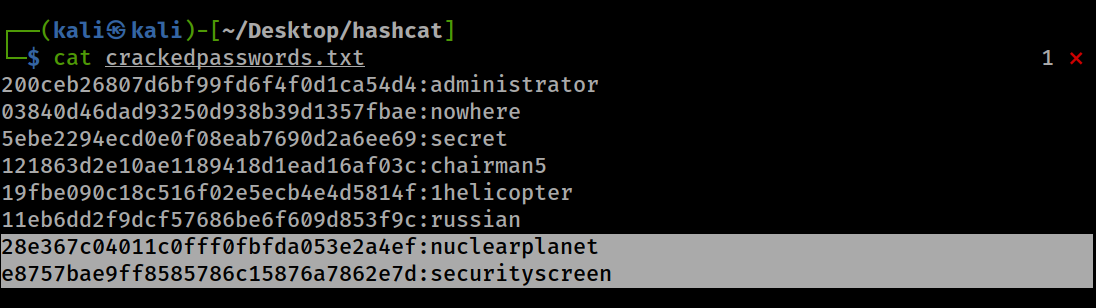
- We can see how a combinator attack has been able to join words from two seperate wordlists and successfully cracked two more hashes.
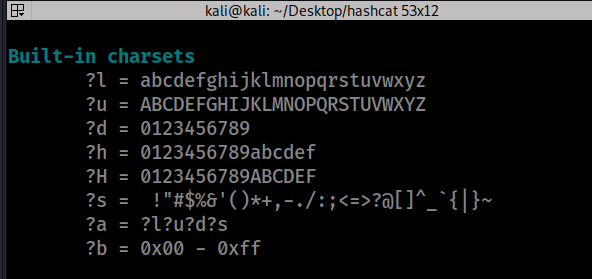
4. Brute-force Attack Brute-force attacks use masks (built-in charsets) to set the range and type of characters to be combined and used for attacks. The image below show the masks. Masks are more efficiently used after some sort of social engineering or if you have an idea of what the password could look like.
For example, In the code block below, we know that the password is a 6-digit zip code, but we don’t know what those 6-digits are so we specify ‘?d’ to only combine numbers 0 - 9 and we specify it six times ‘?d?d?d?d?d?d’ because we know that the password contains 6 characters.
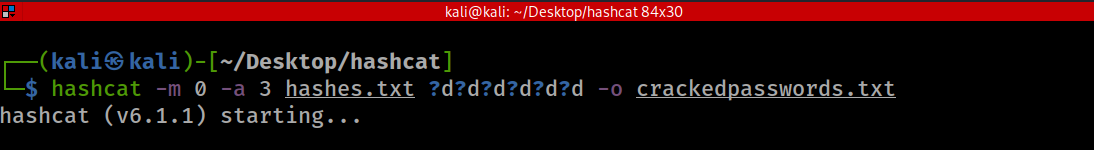
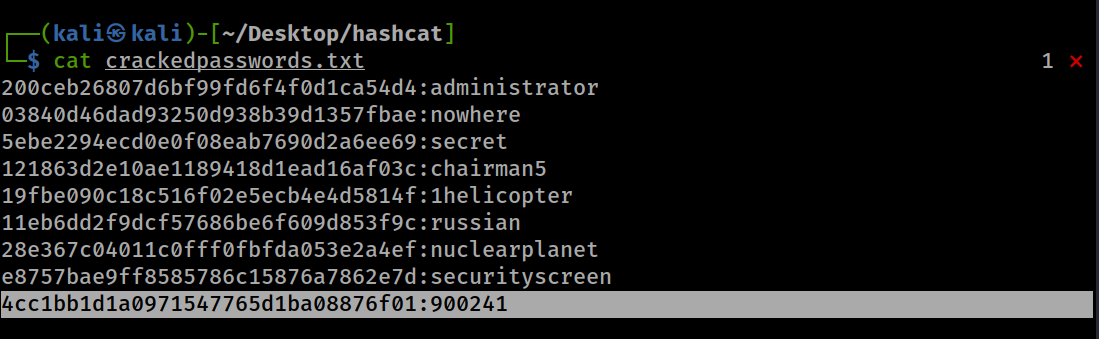
With that combination, we were able to brute-force and crack another hash as shown above.
In the case where we do not know the exact length of characters or even the type of characters, we can use the increment argument ‘-i’ before the mask to try single digit characters up to a specified maximum length of characters. We also use ‘?a’ because it checks all types of characters. Note that the increment form of attack takes longer to finish and the higher the upper limit of the password length, the longer the cracking process. In the code block below, we assume that the password is not more than 5 characters and we don’t know the types of characters the password contains so we increment from 0 to 5 characters by using ‘-i ?a?a?a?a?a’
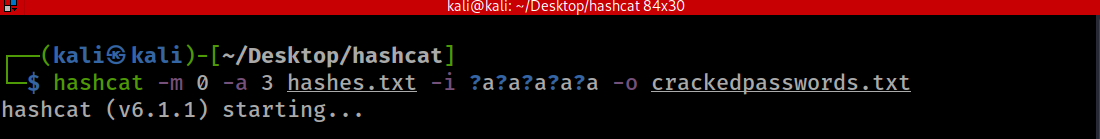
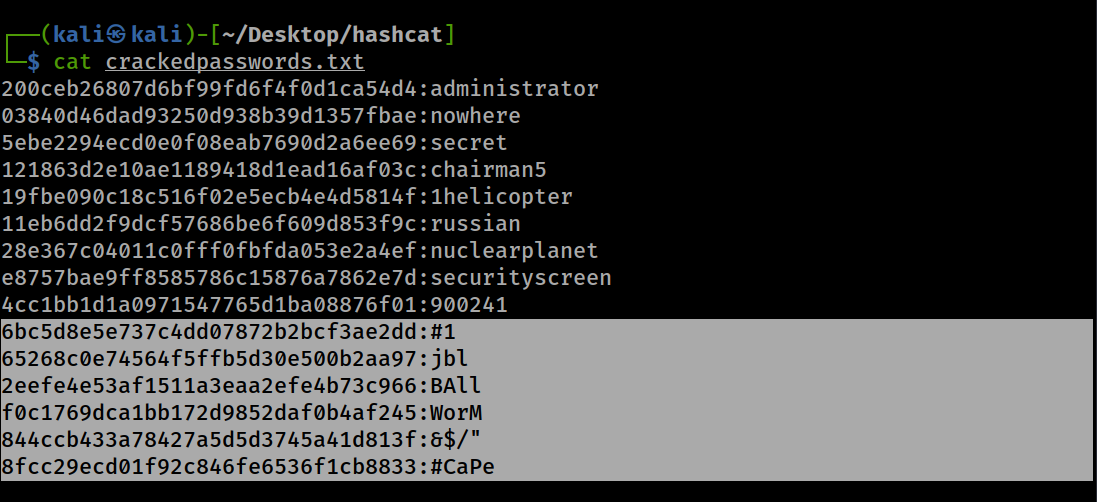
We can see that we were able to crack the rest of the hashes from two characters to five characters containing all kinds of characters.
Your take-away from all of this Use lengthy (at least 10 characters) and unique characters for your passwords.
-
Lengthy because lengthy passwords will take decades for a regular hardware to brute-force. No regular human has decades to spend just cracking one password and not very many people have supercomputers.
-
Unique so that your password will not be present in any wordlist. Popular song lyrics although very lengthy can be found in wordlists, so make sure your password is unique. You can use your own song lyrics if your song isn’t a hit song.
You can go here to make unique and lengthy passwords. You can also use in-browser password suggestions to make passwords and use password managers store them and help you remember them.
References [1]”Hashcat”. Hashcat. Wikipedia [2]”hashcat v3.00”. Hashcat. Hashcat project. 29 June 2016. [3]”Recent Developments in Password Cracking”. Passwords. Bruce Schneier. 19 September 2012. [4]”Hashing Algorithms”. Hashing Algorithms. Jscrambler. 12 August 2020.
External Links More on Masks - https://www.unix-ninja.com/p/Exploiting_masks_in_Hashcat_for_fun_and_profit
Learn about rules and rule-based attacks - https://www.armourinfosec.com/performing-rule-based-attack-using-hashcat/
Unique password generator - https://passwordsgenerator.net/
Images 6-digit brute-force attack - https://raw.githubusercontent.com/CincChou/Markdown-Photos-For-Hacking/main/brute_force_attack.jpg
Wordlist attack - https://raw.githubusercontent.com/CincChou/Markdown-Photos-For-Hacking/main/dictionary_attack.jpg
Hashtypes in hashcat - https://static.wixstatic.com/media/6a4a49_9c2cd04a1ec245dea26343ed18e6e839~mv2.jpg/v1/fill/w_686,h_540,al_c,lg_1,q_90/6a4a49_9c2cd04a1ec245dea26343ed18e6e839~mv2.webp
Attack modes in hashcat - https://laconicwolf.com/wp-content/uploads/2018/09/hashcat_tutorial_003.png
Sha1 hash function - https://blog.jscrambler.com/content/images/2016/12/cryptographic-hash-function.png