MiTM Attack with Ettercap
Background
 [1]
[1]
Man in the middle attack is one of the oldest forms of cyberattacks. Computer scientists have been looking at ways to prevent this type of attack since the early 1980s. [2]
If attackers can place themselves between the communication of two systems, they can control the data traffic between the two systems. Once the attacker takes control of the flow of the traffic, they can spy on the traffic, filter the traffic, inject malware scripts and even alter the traffic data. In this presentation, we will show how to use ettercap to achieve MiTM position using ARP poisoning and launch an SSH downgrade attack to demonstrate what this position can do.
Ettercap is an open-sourced network security tool kit for man-in-the-middle type attacks. In the early days of its development, Ettercap was developed as a sniffer for LAN use only. As the software gained traction in the network security community, Ettercap gained more features that support both active and passion dissection of many protocols as well as extension features for network and host analysis. If you are interested, the source code of Ettercap can be found on GitHub: (https://github.com/Ettercap/ettercap) ***
List of Features
Most of functions can be managed in Plugins settings
- Character injection into an established connection
- SSH1 support (SSH downgrading)
- HTTPS support (SSLStrip)
- Remote traffic through a GRE tunnel
- Plug-in support
- Password collectors
- Packet filtering/dropping
- OS fingerprinting
- Kill a connection
- Passive scanning of the LAN
- Hijacking of DNS requests.
***
Installation
Ettercap can run in various Unix-like operating systems such as Linux and Mac OS
In Linux:
apt-get install ettercap
In Mac:
First install brew:
/bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/HEAD/install.sh)"
Then install ettercap:
brew install ettercap
How Ettercap Works
Ettercap has two main sniffing options, passive and active sniffing.
UNIFIED:
This method works essentially the same as Wireshark. It sniffs all the packets that pass on the cable. You can choose to put the interface in promisc mode. The packet not directed to the host running ettercap will be forwarded automatically using layer 3 routing. So you can use a mitm attack launched from a different tool and let ettercap modify the packets and forward them for you.
BRIDGED:
This mode forwards the traffic from one to the other using two network interfaces. While forwarding traffic, it also performs sniffing and packet filtering to the traffic. This sniffing method is stealthy since there is no way to find that someone is in the middle on the cable. You can look at this method as a mitm attack at layer 1. You will be in the middle of the cable between two entities. [3] ***
APR poisoning
Goal: Get into a man-in-the-middle position.
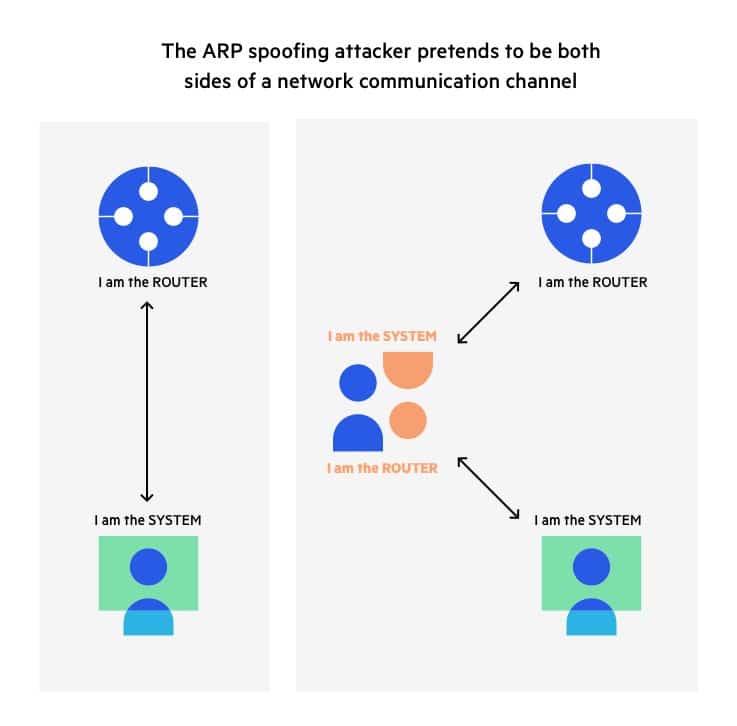 [4]
[4]
To do that, we need to trick the victim’s computer into thinking I am the router so the victim’s computer can send me packets. At the same time, I also need to trick the router to think I am the victim computer so the router can forward me packets I am not supposed to see. To achieve this, we use ARP poisoning.
APR, address resolution protocol, is a protocol that allows Internet communication to reach a specific device on the network. Essentially, ARP translates Internet protocol addresses to Media Access Control (Mac) addresses, and vice versa.
Hosts (victim computers) maintain an ARP cache that maps between IP address and Mac address. If the host doesn’t know the Mac address for an IP address, the host will send out an ARP request packet and ask for the matching MAC address.
However, ARP didn’t design with security in mind, it doesn’t verify if a response of an ARP request actually comes from an authorized party. The protocol also allows hosts to accept ARP responses and add them to the ARP cache even the host computer never sent out requests. This weak point allows ARP poisoning attacks.
Procedure
- Assuming Attacker in the same network as the victims. Attacker can scan the network to find the IP address of the victim’s computer and router.
- Open ipv4 packet forwarding (ARP protocol only work in ipv4 protocol)
- Uses Ettercap to send out fake ARP responses to the network.
- The fake ARP response advertises that the correct MAC address for both IP address(router and victim’s computer) is the attacker’s MAC address.
- both the router and the victim’s computer update their ARP cache. From this point on, both the router and victim’s computer connect to the attacker’s computer instead of each other.
- Attacker can now in the middle of all communication, he can intercept all packets and decide if a packet can forward to the router. [3]
***
SSH Downgrading
Goal: Force the client and server downgrade and use SSH-1 if the SSH version is 1.99. Then use ettercap to extract SSH-1 username and password.
SSH, Secure Shell, is a cryptographic network protocol that let network services operate securely over an unsecured network. SSH was initially developed in 1995 when people realized that they required a more secure communication protocol than plain text. SSH was updated to version 1.5 later and widely spread. However, SSH 1.5, usually referred to as SSH-1, has inherent flaws. SSH-2 fixed those security holes, but a few servers support both SSH-1 and SSH-2. RFC 4253 specified the server should identify its protocol version as 1.99, if both of them are supported. The server is definitely going to use a safer protocol if possible, but it is still likely to exploit the vulnerability if we can establish the connection with the SSH-1 protocol.
In typical cases, when a client wants to connect to an SSH server, the SSH server will inform the client that it supports SSH-1.99 (if not, there is no choice) after the TCP 3-way handshake. Since we already achieved the MiTM position using ARP poisoning, we could rewrite the message from the server that the server supports SSH-1 only, the client will try to establish the connection with SSH-1 protocol.
 [5]
[5]
Procedure:
-
Assuming the victim has been ARP poisoned. In the attacker machine, go to the location of ettercap.
Assumeing in Debian:
cd /user/share/ettercap -
Compile an ettercap SSH filter that captures the SSH-2 request packets and rewrite it into a SSH-1 request packet
sudo etterfilter etter.filter.ssh -o etter.filter.ssh.co -
Load the compiled filter through >Filters or run the script in the prompt:
sudo ettercap -T -q -i eth0 -M arp -F etter.filter.ssh.co -
Once executed,ettercap will monitor the victim’s computer for SSH request packets. If the user enter SSH username and password for a server, ettercap will automatically capture and display the username and password to the attacker
Prevention:
ARP Poisoning
-
Use VPN
If you are travelling frequently and use public wifis, using a VPN can prevent ARP spoofing. VPN uses an encrypted tunnel that blocks activities from ARP spoofing hackers.
-
Use Static ARP
If you have two hosts that communicate with each other frequently, creating a static ARP entry on both hosts can reduce the risk of ARP spoofing. [6]
SSH Downgrading
-
To prevent servers from abusing, the best choice is to stop the support of SSH-1 from the server side, namely, to adapt protocol SSH-2 only.
Reference
[1] J. Umawing and J. Umawing, “When three isn’t a crowd: Man-in-the-Middle (MitM) attacks explained - Malwarebytes Labs”, Malwarebytes Labs, 2021. [Online]. Available: https://blog.malwarebytes.com/101/2018/07/when-three-isnt-a-crowd-man-in-the-middle-mitm-attacks-explained/. [Accessed: 13- Mar- 2021].
| [2] “Password authentication with insecure communication | Communications of the ACM”, Dl.acm.org, 2021. [Online]. Available: https://dl.acm.org/doi/10.1145/358790.358797. [Accessed: 13- Mar- 2021]. |
[3] “Ubuntu Manpage: ettercap - multipurpose sniffer/content filter for man in the middle attacks”, Manpages.ubuntu.com, 2021. [Online]. Available: http://manpages.ubuntu.com/manpages/bionic/man8/ettercap.8.html. [Accessed: 13- Mar- 2021].
| [4] “What is ARP Spoofing | ARP Cache Poisoning Attack Explained | Imperva”, Learning Center, 2021. [Online]. Available: https://www.imperva.com/learn/application-security/arp-spoofing/. [Accessed: 13- Mar- 2021]. |
[5] “SSH MitM Downgrade”, click death squad, 2021. [Online]. Available: https://80ed61ba-a-62cb3a1a-s-sites.googlegroups.com/site/clickdeathsquad/Home/cds-ssh-mitmdowngrade/ssh-mitmattack.jpg?attachauth=ANoY7comTSZRSscD8NXzL09mLKhSbnMlxBAPD8iEws9M-4nrWbIV-pNHCwFDUXhpj891ohe7oeG9qcvkLgm6uCD-7skKukiHu8LnyKOHk4pxS3oyqJEfQG5_Py7oSKHTyDp5s73OSP8N3kN0PdQLHnLMFVHqnEjNtt1-0q2sIkNTMia8NsyXQes-Wlq9J7bsDJO_Rm5rcgyY1syZNfdQtevqN-H-ur2VmcHKiBq-xMsvc1_JhWxmwSuvenDtHOBe5z4TT59c3tds&attredirects=0. [Accessed: 13- Mar- 2021].
| [6] “ARP Poisoning Attack: How to Prevent ARP Spoofing | Indusface”, Indusface, 2021. [Online]. Available: https://www.indusface.com/blog/protect-arp-poisoning/. [Accessed: 13- Mar- 2021]. |