ECE 9609 / 9069 Introduction to Hacking:Presentation 1: Tool/method case study
Distributed Denial-of-service (DDoS) Attack
Group members: Hancheng Lei(251099234), Siyang Li(251129414)
1.Background
1.1 What is DDoS ?
DDoS, or Distributed Denial of Service, is a malicious network attack that involves hackers forcing numerous Internet-connected devices to send network communication requests to one specific service or website with the intention of overwhelming it with false traffic or requests. This has the effect of tying up all available resources to deal with these requests, and crashing the web server or distracting it enough that normal users cannot create a connection between their systems and the server.
1.2 How dose DDoS make it ?
To pull off a DDoS attack, hackers need an army of zombie computers to do their bidding. Hackers use what we call a DDoSTool to enslave computers and build their army. This zombie network of bots (botnet) communicates with the command and control server (C&C), waiting for commands from the hacker who’s running the botnet. In the case of a DDoS attack, it can happen that tens of thousands or even millions of bots work simultaneously to send large amounts of network traffic in the direction of the target server and the server cannot deal with so many requests, so the nomal request cannot reach the server.
1.3 Who would use it or would want to use it ?
The motivations behind attacking a website or service vary. Hactivists will use a DDoS to make a political statement against an organization or government. There are criminals who do it to hold a commercial website hostage until they receive a ransom payment. Unscrupulous competitors have employed a DDoS to play dirty against rival companies.
1.4 Why does hackers choose DDoS ?
Unlike other malicious data tampering or hijacking attacks, DDoS is simple and crude, which can directly destroy the target. In addition, compared with other attack means, the technical requirements of DDoS and the cost of launching the attack are very low. It only needs to buy part of the server permissions or control a batch of broilers, and the attack speed is very fast, and the attack effect is visible. On the other hand, DDoS is easy to attack and difficult to defend. In order to meet the needs of normal customers, service providers need to spend a lot of resources to fight against the attack initiator. These characteristics make DDoS a good sword in the hands of hackers, and a thunderbolt to them.
On the other hand, although DDoS can erode bandwidth or resources and force service interruption, it is far from the true purpose of hackers. The so-called “no sale, no killing”. DDoS is just a nuclear weapon in the hands of hackers. Their purpose is either extortion, commercial competition, or to express their political position. Driven by this kind of black interests, more and more people participate in the industry and upgrade the attack means, which makes DDoS increasingly fierce in the Internet industry and becomes a stubborn disease that can not be overcome in the world.
1.5 How do DDoS attacks affect businesses?
Obviously, a company or retail commercial website has to take DDoS threats seriously.
As Malwarebytes expert Pieter Arntz writes, “Depending on the type and size of your organization, a DDoS attack can be anything from a small nuisance to something that can break your revenue stream and damage it permanently. A DDoS attack can cripple some online businesses for a period of time long enough to set them back considerably, or even put them out of business completely for the length of the attack and some period afterwards. Depending on the kind of attack, there can also be—intentional or not—side effects that can further hurt your business.”[^1]
Side effects of a DDoS include:
- Disappointed users who may never return
- Data loss
- Loss of revenue
- Compensation of damages
- Lost work hours/productivity
- Damage to the business’s reputation
2.Technical Content
2.1 Attack
2.1.1 What is DoS attack?
Using some defects of network protocol, the web server is filled with a large amount of information (useless), which consumes the network bandwidth or system resources. As a result, the network or system is overloaded and paralyzed, and stops providing normal network services.
2.1.2 What is DDoS attack?
DDoS is a DOS based denial of service attack.
A complete DDoS attack system consists of attacker, master, agent and attack target. The main control side and the proxy side are used to control and actually launch attacks respectively. The main control side only issues commands and does not participate in the actual attack. The proxy side issues the actual attack packets ofDDoS, and the main control side issues the commands to each proxy host. Each attack agent host will send a large number of service request packets to the target host, and the services requested by these packets often consume a lot of system resources, resulting in the target host unable to provide normal services for users, resulting in network system paralysis.
2.1.3 DOS vs DDoS Attack[^2]
2.1.4 The method of DDoS attack:
a) Resource consumption attack Syn Flood Attack[^3]
A SYN flood is a form of denial-of-service attack in which an attacker rapidly initiates a connection to a server without finalizing the connection. The server has to spend resources waiting for half-opened connections, which can consume enough resources to make the system unresponsive to legitimate traffic.
Steps:
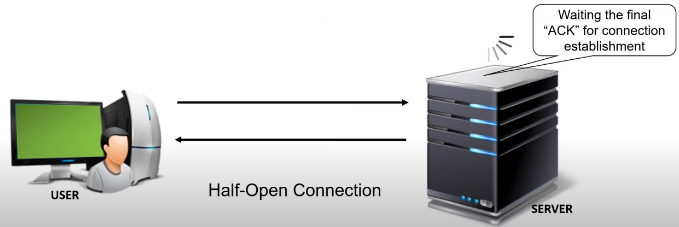
Starting the second step of “Three-way Handshake” procedure and as long as the “Three-way Handshake” procedure is not completed and terminated, the status of the connection is referred as “Half open connection”. During a “Half open connection”, the destination machine already sent the SYN-ACK packet and it is waiting for the final ACK packet to arrive in order to complete the process and establish the connection. The destination machine will wait for a certain amount of time for final ACK packet to arrive.
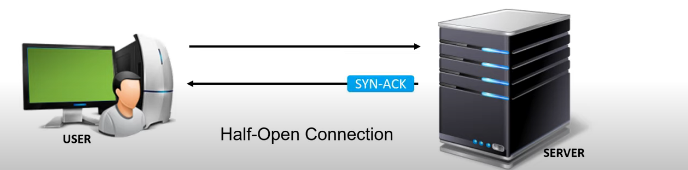
During this time, the information about the pending connection will be registered and processed which will take some amount of memory and processing capabilities at the destination machine.
An attacker exploits this fact by sending an extensive amount of SYN packets (a part of TCP’s three-way handshake used to establish a connection.) in a very high rate aiming to consume most resources (memory and processing capabilities) of the target machine, thus make it unavailable for other, legitimate connection requests.
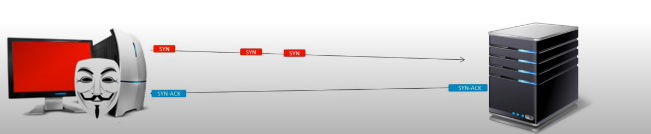
If the attacker will use its own IP as a source address, each SYN packet sent will be answered with SYN-ACK packet from the server, flooding the attacker himself.

IP Address spoofing is a key principle for conducting a successful SYN-Flood attack. By spoofing the source the address, an attacker can flood the target will SYN packets while ensuring all “SYN-ACK” answers will be sent back to spoofed IP addresses which will never answer the final “ACK” packet.
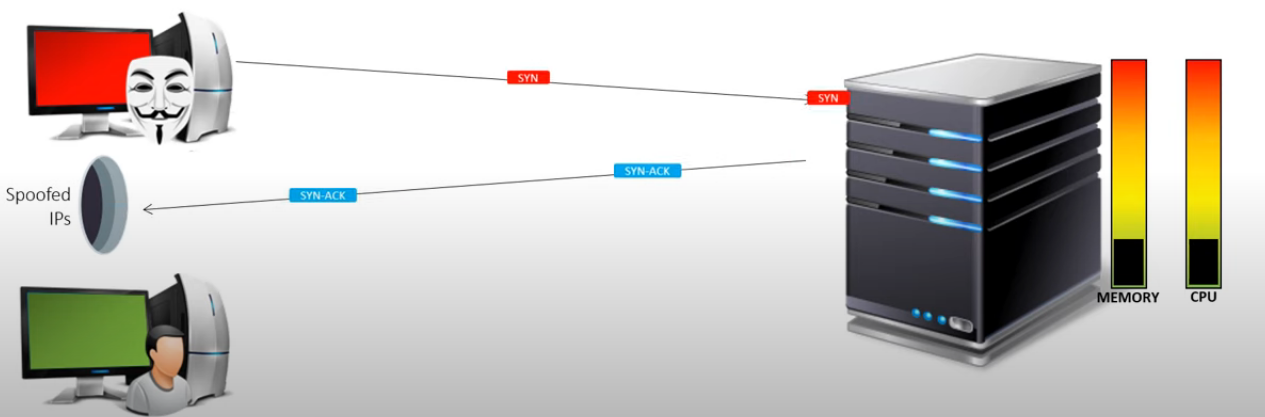
By doing so, the attacker can consume memory & CPU on the target machine, making it unavailable for legitimate connection requests.
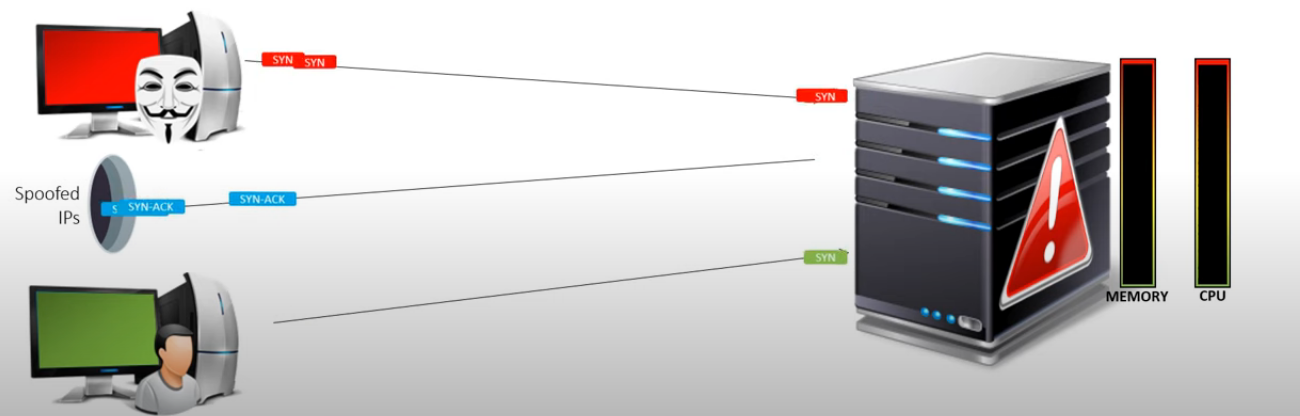
Tutorial: SYN flood attack demo
Ack Flood Attack[^4]
An ACK flood attack is when an attacker attempts to overload a server with TCP ACK packets. Like other DDoS attacks, the goal of an ACK flood is to deny service to other users by slowing down or crashing the target using junk data.
UDP Flood Attack[^5]
A UDP flood is a type of denial-of-service attack in which a large number of User Datagram Protocol (UDP) packets are sent to a targeted server with the aim of overwhelming that device’s ability to process and respond. The firewall protecting the targeted server can also become exhausted as a result of UDP flooding, resulting in a denial-of-service to legitimate traffic.
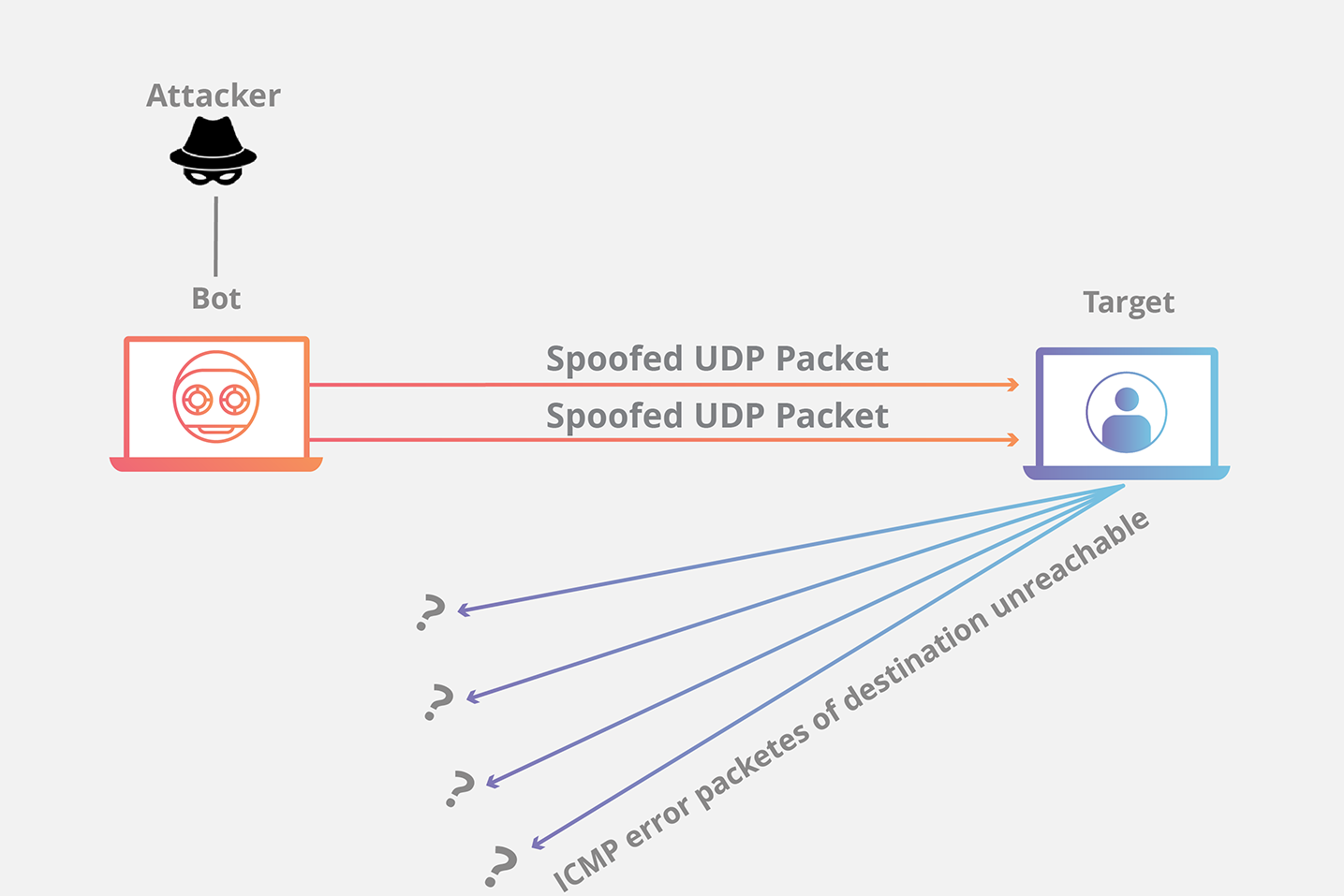
b) Service consumption attack Challenge Collapsar Attack
CC attack (Challenge Collapsar Attack) is an attack against web server or application. It uses standard get / post requests to obtain information, such as universal resource identifier (URI) involved in database operation or other URIs that consume system resources, causing the server to run out of resources and fail to respond to normal requests.
In a challenge collapsar (CC) attack, the attacker uses a proxy server to generate and send disguised requests to the target host. In addition, the attacker controls other hosts in the Internet and makes them send large numbers of data packets to the target server to exhaust its resources. In the end, the target server stops responding to requests. As you know, when many users access a web page, the page opens slowly. So in a CC attack, the attacker simulates a scenario where a large number of users (a thread represents a user) are accessing pages all the time. Because the accessed pages all require a lot of data operations (consuming many CPU resources), the CPU usage is kept at the 100% level for a long time until normal access requests are blocked.
c) Reflection attack DNS Reflection Attack[^6]
Ideally, DNS servers only provide services to machines within a trusted domain. But DNS reflection attacks rely on consumer and business routers and other devices equipped with DNS servers that are (mis)configured to accept queries from anywhere on the Web. Attackers can send spoofed DNS queries to these so-called “open recursive” DNS servers, forging the request so that it appears to come from the target’s network. That way, when the DNS servers respond, they reply to the spoofed (target) address.
The bad guys also can amplify a reflective attack by crafting DNS queries so that the responses are much bigger than the requests. They do this by taking advantage of an extension to the DNS protocol that enables large DNS messages. For example, an attacker could compose a DNS request of less than 100 bytes, prompting a response that is 60-70 times as large. This “amplification” effect is especially pronounced if the perpetrators query dozens of DNS servers with these spoofed requests simultaneously.
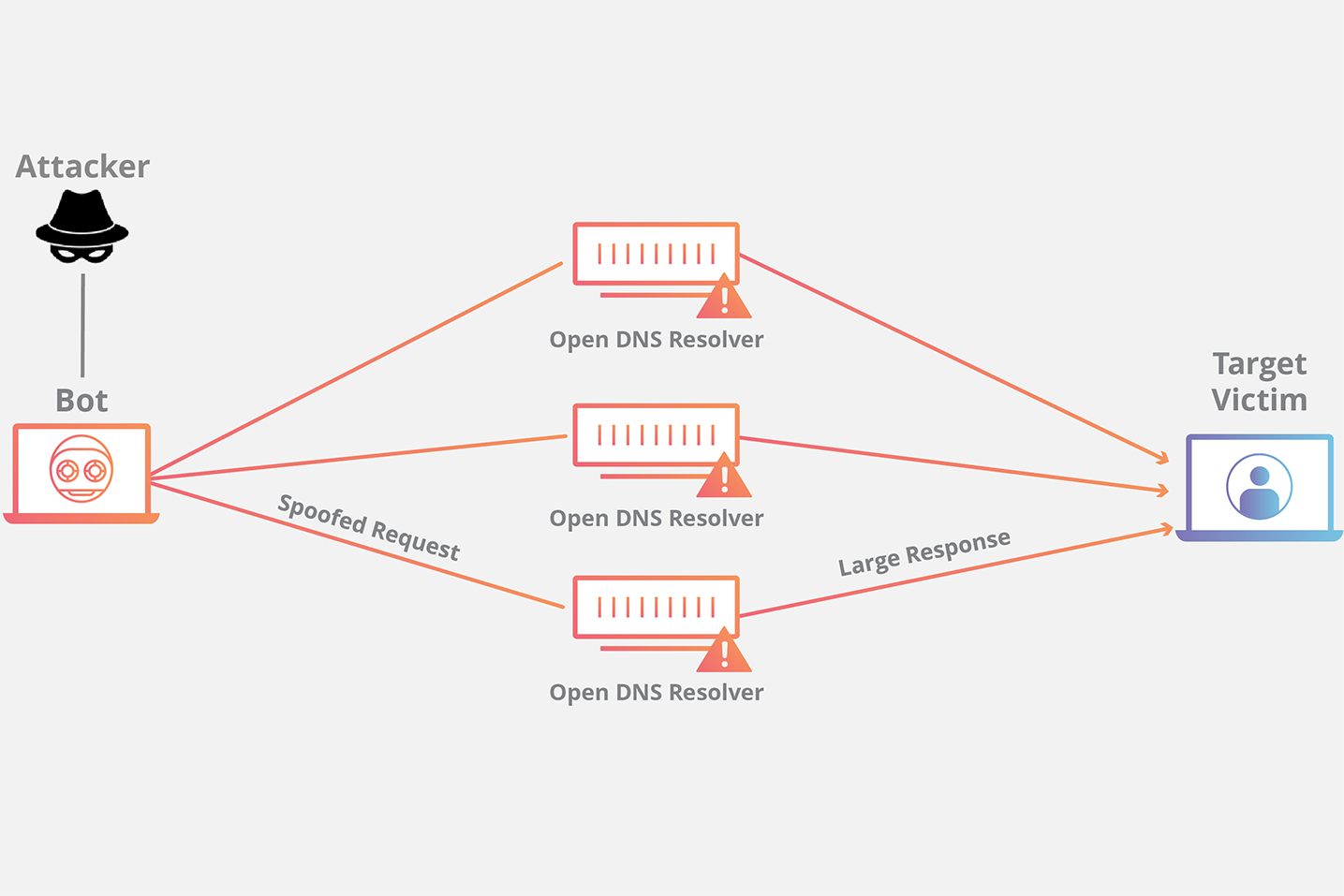
d) Hybrid attack
In the actual situation, attackers only want to achieve the purpose of destroying the other party. Up to now, advanced attackers are no longer inclined to use a single attack method. Instead, they flexibly combine a variety of attack methods according to the specific environment of the target system. They not only have a large amount of traffic, but also make use of the defects of the protocol and system to launch the attack as much as they can.
2.2 Defence
2.2.1 How do I prevent being a part of a botnet?
To avoid becoming an unwilling and unwitting participant in a botnet-fueled DDoS, practice the same good computer hygiene for preventing all malware infections: keep your operating system and apps up to date, and don’t click on unknown links and unexpected attachments.
And of course, real-time, always-on cybersecurity is a hard-and-fast must-have to protect you from DDoSTool downloads and all other associated malware threats.
2.2.2 How does a company prevent being attacked by DDoS?
- a) Develop a Denial of Service Response Plan
- b) Secure Your Network Infrastructure
- c) Practice Basic Network Security
- d) Maintain Strong Network Architecture
- e) Leverage the Cloud
3. Related news about DDoS
- The AWS DDoS Attack in 2020[^7]
Amazon Web Services, the 800-pound gorilla of everything cloud computing, was hit by a gigantic DDoS attack in February 2020. This was the most extreme recent DDoS attack ever and it targeted an unidentified AWS customer using a technique called Connectionless Lightweight Directory Access Protocol (CLDAP) Reflection. This technique relies on vulnerable third-party CLDAP servers and amplifies the amount of data sent to the victim’s IP address by 56 to 70 times. The attack lasted for three days and peaked at an astounding 2.3 terabytes per second.
- The GitHub Attack in 2018[^8]
On Feb. 28, 2018, GitHub—a platform for software developers—was hit with a DDoS attack that clocked in at 1.35 terabits per second and lasted for roughly 20 minutes. According to GitHub, the traffic was traced back to “over a thousand different autonomous systems (ASNs) across tens of thousands of unique endpoints.”
Even though GitHub was well prepared for a DDoS attack their defenses were overwhelmed—they simply had no way of knowing that an attack of this scale would be launched. [^9]
4. References
- [^1]Business effects by DDoS Attack, Link.
- [^2]DOS vs DDoS Attack, Link.
- [^3]Syn Flood Attack, Link.
- [^4]Ack Flood Attack, Link.
- [^5]UDP Flood Attack, Link
- [^6]DNS Reflection Attack, Link
- [^7]The AWS DDoS Attack in 2020, Link.
- [^8]The GitHub Attack in 2018, Link.
- [^9]Explaining the GitHub DDoS Attack, Link.